How Do Computer Criminals Attack?

“Data Thief – Hacker – Cyber Criminal” (CC BY-SA 2.0) by perspec_photo88
Hacking, identity theft and malware are some of the more sinister risks associated with using the internet but, with the ready availability of anti-virus software and firewalls online, how do hackers manage to cause so much damage? Here are just two ways criminals use confidence tricks and malware to attack computer users.
Backdoor Attacks
A backdoor in a computer program or website is exactly what it sounds like – a way for hackers to sneak in and out without detection, ignoring login prompts or other authentication systems. This type of attack can be used to steal data, spread malware to other computers, or rope an affected website into a Distributed Denial of Service attack as part of a botnet.
Exploiting a backdoor involves tricking the owner of a PC into installing a backdoor trojan (perhaps as part of a phishing attack) or taking advantage of an existing backdoor in a piece of software installed intentionally for legitimate purposes (remote tech support, for example). A malicious program can also be disguised as a useful app pre-loaded onto new PCs by the manufacturer. For instance, in November, a pre-installed backdoor was discovered on 3 million Android phones (55 different devices) made by BLU, Infinix, Doogee and several other brands. Despite the intervention of a security company, the devices remain vulnerable to Man in the Middle attacks.
Backdoors are very difficult to detect and remove but protection does exist in the form of web application firewalls, an increasingly affordable solution for businesses with an online presence.
Tech Support Scams
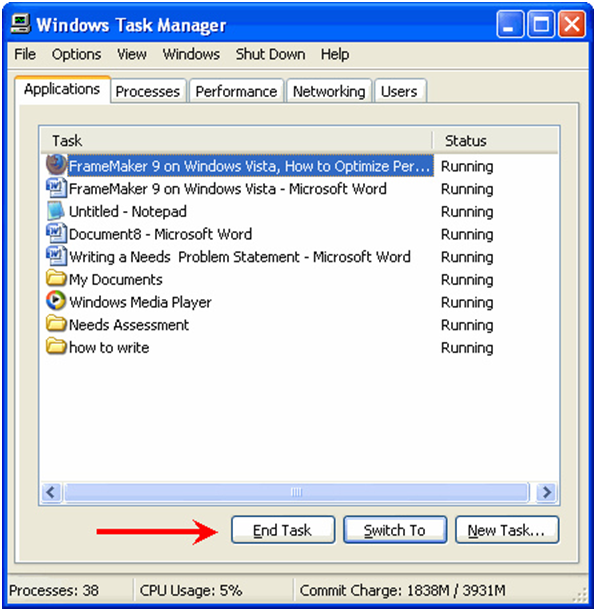
“Using Windows Task Manager to close Adob” (CC BY 2.0) by http://klarititemplateshop.com/
In brief, a tech support scam involves a criminal persuading a computer user to let them access and control their PC remotely. In a lawsuit filed in 2014, Microsoft claimed that this kind of confidence trick costs Americans $1.5 billion each year due to losses from fraudulent use of credit cards and malware (keyloggers, password grabbers, etc.) installed by bogus agents.
Beginning with a phone call or email, the scammer tells the victim that their PC is infected with malware that requires a specialist to be removed, for a large financial commitment and the installation of a remote access application. In many cases though, there is no threat; the caller simply refers the target to obscure (but innocuous) files in the Windows OS.
For example, Windows’ Task Manager, which you can view by pressing Ctrl+Shift+Esc on Windows platforms, lists active processes on your computer. Tech support scammers sometimes point to “too many” processes as evidence of a malware infection, when no such situation exists. Lenny Zeltser, an information security expert who recorded a conversation with a cybercriminal, was told that numbers over forty indicated the presence of viruses and other computer nasties in the processes. In fact, while it is possible to spot adware in particular in the list of processes, even sterilised PCs can have many more than forty active.
As a final point, it’s worth mentioning that there are a number of ways that hackers can gain access to a computer – emails containing viruses, websites loaded with trojans, malicious code in advertisements, and pre-packaged malware in software – so it’s important to keep security software and all applications up-to-date. Indeed, whether it’s for farming personal details or overloading websites with traffic, all devices linked to the internet are valuable to cybercriminals.










